Announcing the General Availability of SQL Diagnostic Manager for MySQL 8.9.7

Categories
- Free tools
- SQL Compliance Manager
- SQL Defrag Manager
- SQL Diagnostic Manager for MySQL
- SQL Diagnostic Manager for SQL Server
- SQL Diagnostic Manager Pro
- SQL Inventory Manager
- SQL Query Tuner for SQL Server
- SQL Safe Backup
- SQL Secure
- SQL Workload Analysis for SQL Server
- Uptime Infrastructure Monitor Formerly Uptime

Finding Registered Event Log Source Names
Understanding Event Log Source Names When you write events to an event log using Write-EventLog, you must specify a valid source name. However, there is no easy way of finding out which source files are registered for a particular event log. This can also bite you...

Select-Object and -ExcludeProperty
Here is a line of code that often puzzles PowerShell users: Get-Service | Select-Object -ExcludeProperty Name Understanding the -ExcludeProperty Behavior When you use Select-Object, its -ExcludeProperty parameter does not seem to do anything. The truth is:...

Converting PowerShell to Batch
Here is a fun PowerShell function called Convert-PowerShellToBatch. Provide it with the path to a PowerShell script, or pipe in the results from Get-ChildItem to batch-convert many scripts. How It Works: Batch File Generation The function creates a batch file per...

How to monitor Always On availability groups
Always On availability groups are part of an integrated solution with the goal of achieving the highest level of data availability and disaster recovery for organizations. Availability groups grant database administrators the ability to automatically or manually...

How to monitor and diagnose SQL query performance
Executing resource-intensive SQL queries requires a significant amount of processor time, memory, and bandwidth, and storage. Resource-intensive SQL queries prevent other SQL queries from using these resources. This can eventually lead to blocking. Common causes of...

Converting User Name to SID
If you’d need to find out the SID for a user name, here is a useful chunk of code that does the job: $domain =…

Displaying Data in a Grid View Window Vertically
Out-GridView always produces a table with one object per line: Get-Process -Id $pid | Out-GridView Occasionally, it would be more helpful to display the object…

Alert Configuration Templates in SQL Diagnostic Manager
Introduction to Alert Configuration Templates Several versions ago, SQL Diagnostic Manager (SQLDM) introduced Alert Configuration Templates, which basically allowed users to preconfigure alert settings (metrics which are to be alerted upon and the thresholds set for...
Finding All Domain Controllers (no module required)
Reviewing the ActiveDirectory Module Approach In the previous tip we explained how you can use the ActiveDirectory module and its cmdlets to find all domain controllers in your organization, or perform any other LDAP query. Leveraging Pure .NET Methods Here is the...

Getting Cached Credentials
Managing Cached Credentials with PSCredentialManager In the previous tip we talked about a public module called PSCredentialManager that helps you manage cached credentials. Sometime, less is more, so when you look at the code you’ll soon discover that it is a...

Installing Modules in PowerShell Core on Linux
Installing PowerShell Modules with Administrator Privileges When you’d like to install modules for all users from the PowerShellGet repository, you need Administrator privileges. On PowerShell Core on Linux, you can use the command “sudo” to enable Administrator...

Parsing Distinguished Names
Using Split() for Parsing Distinguished Names Distinguished names are strings, and strings contain powerful ways of parsing data. The most powerful yet simple approach is the Split() method. Extracting the Last Element with Split() Check out how easy it is to get back...

IDERA ER/Studio Repository Database Setup and Ports – Part 1 – SQL Server
Howdy! In this latest blog post, I will be covering the Database setup one would need for our IDERA ER/Studio Repository. Pre-requisites: SQL Server 2012-2016 (Standard and Above) SQL Server Configuration Manager Enable TCP Ports The default port is 1433. You...

Registering Default PowerShell Repository
Using PowerShellGet to Install Scripts and Modules If you use the PowerShellGet module (which ships by default on Windows 10 and Server 2016), you can easily download and install shared PowerShell scripts and modules: PS> Find-Module -Tag Security Version Name...
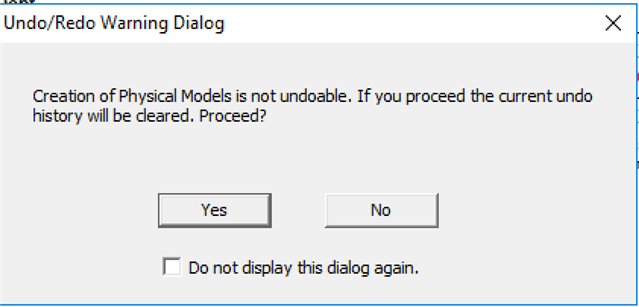
Logical to Physical Data Modeling
In the last article we learned how to create a data model from scratch using ER/Studio Data Architect. In part II we will explore about how to convert a Logical Data Model into a Physical Data Model. See also: IDERA's Guide to the Three Types of Data Model:...

Running PowerShell Script as a Scheduled Task
Scheduling PowerShell Scripts for Automatic Execution If you need to run a PowerShell script in regular intervals, why not run it as a scheduled task? Here are some lines that help you create a new scheduled task to run a PowerShell script at 6AM: #requires -Modules...
Join the Team – Talk Back
Those of you who have endured a product roadmap session with me know that the insight into our direction comes with a price. That price is me badgering you about your own plans and priorities, how you plan to use any suggestions you make, whether you agree with...

Getting the Most from Your Software Vendor
This topic is relevant to more than just Idera and it comes from experience working for and with multiple software vendors in multiple industries. The simple realization is that certain customers seem to know how to gain advantages beyond the purchases and...
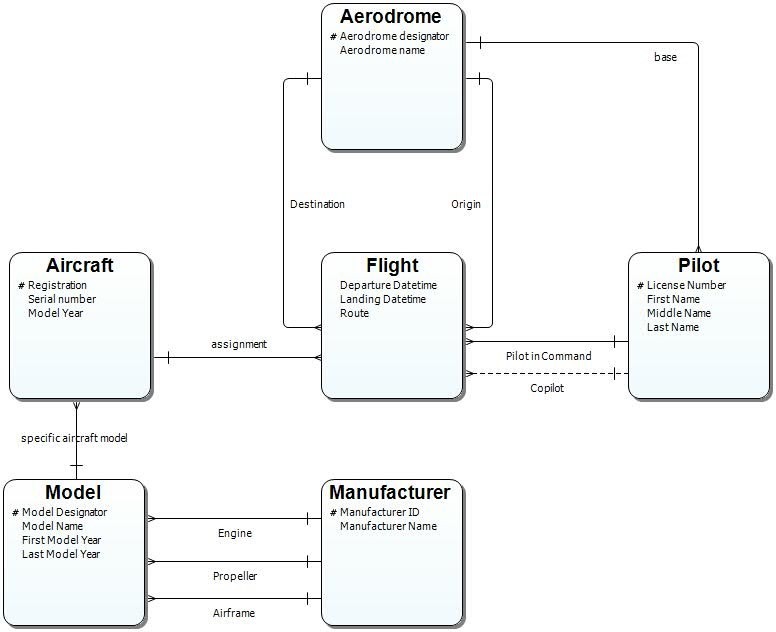
Modeling Graph Data Stores in ER/Studio
Modeling Background Enterprise data environments have become increasingly complex due to a proliferation of different technologies and data platforms. A given organization may have hundreds of different data stores including multiple relational database...

Creating Random MAC Addresses
Randomly Generated MAC addresses If you just need a bunch of randomly generated MAC addresses, and you don’t care much about whether these addresses are actually valid, then here is a one liner: PS> (0..5 | ForEach-Object { '{0:x}{1:x}' -f (Get-Random -Minimum 0...
